- Joined
- Jun 12, 2014
- Messages
- 354
Procedure for PRELOADER MODE no need testpoint
1-open hydra tool
2-select mediatek
3-brand
4-model
5-option
6-dowload/agent(DA)
7-Patch DA
8-DA Option
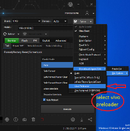
9-select Vivo Preloader
10-done
action taken
Boot info:
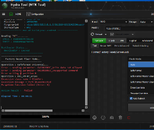
now set in PRELOADER MODE
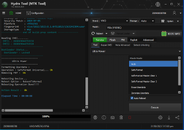
Boot info again succes
klick Ultra Power
1-open hydra tool
2-select mediatek
3-brand
4-model
5-option
6-dowload/agent(DA)
7-Patch DA
8-DA Option
9-select Vivo Preloader
10-done
action taken
Boot info:
Proceed to Format but errorHydra Tool Ver 2023.8.30.0
Windows 10 (Version 22H2, OS Build 19045.3324, 64-bit Edition)
Intel(R) Celeron(R) CPU N3450 @ 1.10GHz
Intel(R) HD Graphics
Ram Installed : 4 GB
Windows Access Right : Admin
Software Run As Admnistrator
******* Dongle Info *******
Version : Hydra Tool v 1.2
Serial : 200900008788
Initialize : OKAY
Status : Activated
Life : 0 [0-0-0-0-0]
-------------------------------------------------------
To Enable BROM Mode :
Method 1 - Bootkey (Vol + - Power) or any combination
Method 2 - Enable Preloader to brom(crashing Method)
Method 3 - Test Point Data0 + ground
To Enable Preloader Mode :
Method 1 - Just Insert cable
-------------------------------------------------------
Searching for MTK Device...Found
MTK Port Type : Flashmode BROM
FriendlyName : MediaTek USB Port (COM9)
Device : /5&32dbfa55&0&3
SymbolicName : \\?\usb#vid_0e8d&pid_0003#5&32dbfa55&0&3#{a5dcbf10-6530-11d2-901f-00c04fb951ed}
Driver Ver : 01/22/2015,3.0.1504.0
Service : wdm_usb
Openning Port [COM9] Ok
Handshaking...Ok
HwCode : 0766 {MT6765/MT8768t}
Hwver : 0000
Target config : E5
SBC : 01 (True)
SLA : 00 (False)
DAA : 04 (True)
SWJTAG : 04 (True)
EPP : 00 (False)
CERT : 00 (False)
MEMREAD : 20 (True)
MEMWRITE : 40 (True)
CMD_C8 : 80 (True)
Connection : BROM
HW Subcode : 8A00
HW Subcode : CA00
SW Ver : 0000
ME_ID : 955439B12E4D6852C581D6EA74463439
SOC_ID : 2AAE5443AF4F70B0C51B7EE617D5BE1D5E345F3D4BD5281FFD18D547AB88EC7C
Exploiting Device...
Successfully Exploited..
Handshaking...Ok
Dumping Preloader from Bootrom..
Seeking preloader address..Found @ 0x00200BC4
Starting to dump...
Prel Size : 0x0003D470
Successfully dump preloader.. [C:\Hydra Tool\Boot\PreloaderDump\preloader_k62v1_64_bsp.bin]
Target config : 00
SBC : 00 (False)
SLA : 00 (False)
DAA : 00 (False)
SWJTAG : 00 (False)
EPP : 00 (False)
CERT : 00 (False)
MEMREAD : 00 (False)
MEMWRITE : 00 (False)
CMD_C8 : 00 (False)
Connection : BROM
Preparing Download Agent..[MTK_AllInOne_DA_5.2152.bin]
Uploading Stage 1....
Successfully uploaded stage 1, jumping ..
Executing JUMP_DA Address @ 0x00200000
Jumping to 0x00200000 Ok 0xC0
Successfully received DA sync
ONNECTION_AGENT : brom
DRAM config needed for : 150100445636444D
Sending auto preloader from dump... [preloader_k62v1_64_bsp.bin]
Sending emi data.. [DRAM setup passed.]
Sending emi data succeeded.
Uploading stage 2...
Upload data was accepted. Jumping to stage 2...
Successfully uploaded stage 2
ERAM Size : 0x000000000003A000-232 KB
IRAM Size : 0x0000000100000000-4 GB
EMMC Boot1 Size : 0x0000000000400000-4 MB
EMMC Boot2 Size : 0x0000000000400000-4 MB
EMMC RPMB Size : 0x0000000001000000-16 MB
EMMC USER Size : 0x0000001D1EC00000-116.48 GB
EMMC CID : 150100445636444D4202541D6ADFA56F - DV6DMB
HW-CODE : 0x766
HWSUB-CODE : 0x8A00
HW-VERSION : 0xCA00
SW-VERSION : 0x0
CHIP-EVOLUTION : 0x0
DA-VERSION : 1.0
Speed : high-speed
Error: on sending data: DA hash mismatch
*DA Extensions failed to enable
Reading Partition Table ..
Partition Count : 44
--------------- Reading build.prop content ---------------
Brand : vivo
Vendor : vivo
Model : vivo 1815
Product : k62v1_64_bsp
Manufacturer : vivo
ID : O11019
SDK : 27
Release : 8.1.0
ABI : arm64-v8a
CPU abilist : arm64-v8a,armeabi-v7a,armeabi
Locale : en-US
Description : full_k62v1_64_bsp-user 8.1.0 O11019 1563242384 release-keys
Device : PD1818CF_EX
Display ID : O11019 release-keys
Security Patch : 2019-07-05
Platform : =MTK6765
Fingerprint : vivo/1815/1815:8.1.0/O11019/1563242384:user/release-keys
StorageType : mtp
--------------- end of build.prop content ---------------
Reading IMEI........
IMEI1 : 868869044356938
IMEI2 : 868869044356920
-------------------------------
Bootloader Status...
Bootloader : Locked
-------------------------------
Backing up Security..
- preloader(preloader.bin), 512 KB = Ok [preloader_k62v1_64_bsp.bin]
*Creating Scatter file... C:\Hydra Tool\Backup\MTKBKUP\0766_955439B12E4D6852C581D6EA74463439\Auto\083123185656\6765_Android_scatter.txt
- pgpt(pgpt.bin), 32 KB = Ok
- nvram(nvram.bin), 64 MB = Ok
- nvdata(nvdata.bin), 64 MB = Ok
- frp(frp.bin), 1024 KB = Ok
- protect1(protect1.bin), 8 MB = Ok
- protect2(protect2.bin), 13.469 MB = Ok
- persist(persist.bin), 48 MB = Ok
- proinfo(proinfo.bin), 3 MB = Ok
- nvcfg(nvcfg.bin), 32 MB = Ok
- sec1(sec1.bin), 2 MB = Ok
- seccfg(seccfg.bin), 8 MB = Ok
- lk(lk.bin), 5 MB = Ok
Backup Done!!!
Elapsed Time : 00:01:28

now set in PRELOADER MODE

Boot info again succes
proceed to remove passwordHydra Tool Ver 2023.8.30.0
Windows 10 (Version 22H2, OS Build 19045.3324, 64-bit Edition)
Intel(R) Celeron(R) CPU N3450 @ 1.10GHz
Intel(R) HD Graphics
Ram Installed : 4 GB
Windows Access Right : Admin
Software Run As Admnistrator
******* Dongle Info *******
Version : Hydra Tool v 1.2
Serial : 200900008788
Initialize : OKAY
Status : Activated
Life : 0 [0-0-0-0-0]
-------------------------------------------------------
To Enable BROM Mode :
Method 1 - Bootkey (Vol + - Power) or any combination
Method 2 - Enable Preloader to brom(crashing Method)
Method 3 - Test Point Data0 + ground
To Enable Preloader Mode :
Method 1 - Just Insert cable
-------------------------------------------------------
Searching for MTK Device...Found
MTK Port Type : Flashmode BROM
FriendlyName : MediaTek USB Port (COM9)
Device : /5&32dbfa55&0&3
SymbolicName : \\?\usb#vid_0e8d&pid_0003#5&32dbfa55&0&3#{a5dcbf10-6530-11d2-901f-00c04fb951ed}
Driver Ver : 01/22/2015,3.0.1504.0
Service : wdm_usb
Openning Port [COM9] Ok
Handshaking...Ok
HwCode : 0766 {MT6765/MT8768t}
Hwver : 0000
Target config : E5
SBC : 01 (True)
SLA : 00 (False)
DAA : 04 (True)
SWJTAG : 04 (True)
EPP : 00 (False)
CERT : 00 (False)
MEMREAD : 20 (True)
MEMWRITE : 40 (True)
CMD_C8 : 80 (True)
Connection : BROM
HW Subcode : 8A00
HW Subcode : CA00
SW Ver : 0000
ME_ID : 955439B12E4D6852C581D6EA74463439
SOC_ID : 2AAE5443AF4F70B0C51B7EE617D5BE1D5E345F3D4BD5281FFD18D547AB88EC7C
Exploiting Device...
Successfully Exploited..
Handshaking...Ok
Dumping Preloader from Bootrom..
Seeking preloader address..Found @ 0x00200BC4
Starting to dump...
Prel Size : 0x0003D470
Successfully dump preloader.. [C:\Hydra Tool\Boot\PreloaderDump\preloader_k62v1_64_bsp.bin]
Target config : 00
SBC : 00 (False)
SLA : 00 (False)
DAA : 00 (False)
SWJTAG : 00 (False)
EPP : 00 (False)
CERT : 00 (False)
MEMREAD : 00 (False)
MEMWRITE : 00 (False)
CMD_C8 : 00 (False)
Connection : BROM
Preparing Download Agent..[MTK_AllInOne_DA_5.2152.bin]
Uploading Stage 1....
Successfully uploaded stage 1, jumping ..
Executing JUMP_DA Address @ 0x00200000
Jumping to 0x00200000 Ok 0xC0
Successfully received DA sync
ONNECTION_AGENT : brom
DRAM config needed for : 150100445636444D
Sending auto preloader from dump... [preloader_k62v1_64_bsp.bin]
Sending emi data.. [DRAM setup passed.]
Sending emi data succeeded.
Uploading stage 2...
Upload data was accepted. Jumping to stage 2...
Successfully uploaded stage 2
ERAM Size : 0x000000000003A000-232 KB
IRAM Size : 0x0000000100000000-4 GB
EMMC Boot1 Size : 0x0000000000400000-4 MB
EMMC Boot2 Size : 0x0000000000400000-4 MB
EMMC RPMB Size : 0x0000000001000000-16 MB
EMMC USER Size : 0x0000001D1EC00000-116.48 GB
EMMC CID : 150100445636444D4202541D6ADFA56F - DV6DMB
HW-CODE : 0x766
HWSUB-CODE : 0x8A00
HW-VERSION : 0xCA00
SW-VERSION : 0x0
CHIP-EVOLUTION : 0x0
DA-VERSION : 1.0
Speed : high-speed
Error: on sending data: DA hash mismatch
*DA Extensions failed to enable
Reading Partition Table ..
Partition Count : 44
--------------- Reading build.prop content ---------------
Brand : vivo
Vendor : vivo
Model : vivo 1815
Product : k62v1_64_bsp
Manufacturer : vivo
ID : O11019
SDK : 27
Release : 8.1.0
ABI : arm64-v8a
CPU abilist : arm64-v8a,armeabi-v7a,armeabi
Locale : en-US
Description : full_k62v1_64_bsp-user 8.1.0 O11019 1563242384 release-keys
Device : PD1818CF_EX
Display ID : O11019 release-keys
Security Patch : 2019-07-05
Platform : =MTK6765
Fingerprint : vivo/1815/1815:8.1.0/O11019/1563242384:user/release-keys
StorageType : mtp
--------------- end of build.prop content ---------------
Reading IMEI........
IMEI1 : 868869044356938
IMEI2 : 868869044356920
-------------------------------
Bootloader Status...
Bootloader : Locked
-------------------------------
Backing up Security..
- preloader(preloader.bin), 512 KB = Ok [preloader_k62v1_64_bsp.bin]
*Creating Scatter file... C:\Hydra Tool\Backup\MTKBKUP\0766_955439B12E4D6852C581D6EA74463439\Auto\083123185656\6765_Android_scatter.txt
- pgpt(pgpt.bin), 32 KB = Ok
- nvram(nvram.bin), 64 MB = Ok
- nvdata(nvdata.bin), 64 MB = Ok
- frp(frp.bin), 1024 KB = Ok
- protect1(protect1.bin), 8 MB = Ok
- protect2(protect2.bin), 13.469 MB = Ok
- persist(persist.bin), 48 MB = Ok
- proinfo(proinfo.bin), 3 MB = Ok
- nvcfg(nvcfg.bin), 32 MB = Ok
- sec1(sec1.bin), 2 MB = Ok
- seccfg(seccfg.bin), 8 MB = Ok
- lk(lk.bin), 5 MB = Ok
Backup Done!!!
Elapsed Time : 00:01:28
klick Ultra Power

DoneHydra Tool Ver 2023.8.30.0
Windows 10 (Version 22H2, OS Build 19045.3324, 64-bit Edition)
Intel(R) Celeron(R) CPU N3450 @ 1.10GHz
Intel(R) HD Graphics
Ram Installed : 4 GB
Windows Access Right : Admin
Software Run As Admnistrator
******* Dongle Info *******
Version : Hydra Tool v 1.2
Serial : 200900008788
Initialize : OKAY
Status : Activated
Life : 0 [0-0-0-0-0]
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Service Function
Ultra Power
Auto
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Searching for MTK Device...Found
MTK Port Type : Flashmode BROM
FriendlyName : MediaTek USB Port (COM9)
Device : /5&32dbfa55&0&3
SymbolicName : \\?\usb#vid_0e8d&pid_0003#5&32dbfa55&0&3#{a5dcbf10-6530-11d2-901f-00c04fb951ed}
Driver Ver : 01/22/2015,3.0.1504.0
Service : wdm_usb
Openning Port [COM9] Ok
Reading Partition Table ..
ERAM Size : 0x000000000003A000-232 KB
IRAM Size : 0x0000000100000000-4 GB
EMMC Boot1 Size : 0x0000000000400000-4 MB
EMMC Boot2 Size : 0x0000000000400000-4 MB
EMMC RPMB Size : 0x0000000001000000-16 MB
EMMC USER Size : 0x0000001D1EC00000-116.48 GB
EMMC CID : 150100445636444D4202541D6ADFA56F - DV6DMB
HW-CODE : 0x766
HWSUB-CODE : 0x8A00
HW-VERSION : 0xCA00
SW-VERSION : 0x0
CHIP-EVOLUTION : 0x0
DA-VERSION : 1.0
Speed : high-speed
Partition Count : 44
--------------- Reading build.prop content ---------------
Brand : vivo
Vendor : vivo
Model : vivo 1815
Product : k62v1_64_bsp
Manufacturer : vivo
ID : O11019
SDK : 27
Release : 8.1.0
ABI : arm64-v8a
CPU abilist : arm64-v8a,armeabi-v7a,armeabi
Locale : en-US
Description : full_k62v1_64_bsp-user 8.1.0 O11019 1563242384 release-keys
Device : PD1818CF_EX
Display ID : O11019 release-keys
Security Patch : 2019-07-05
Platform : =MTK6765
Fingerprint : vivo/1815/1815:8.1.0/O11019/1563242384:user/release-keys
StorageType : mtp
--------------- end of build.prop content ---------------
Reading IMEI........
IMEI1 : 868869044356938
IMEI2 : 868869044356920
-------------------------------
Bootloader Status...
Bootloader : Locked
-------------------------------
---------------------------
Ultra Power
---------------------------
Formatting Userdata :
Operation : Safeformat Universal... Ok
Removing FRP : Ok
Rebooting Device...
Reboot Option : RebootToNormal
Rebooting Operation Done!!!!
Action Result : Ok
Elapsed Time : 00:00:08
