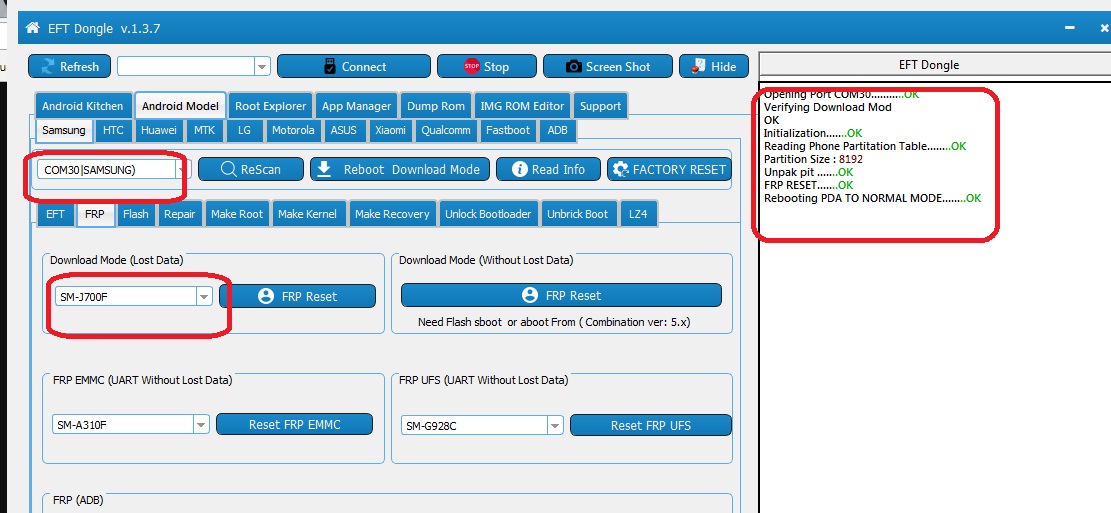
EFT Dongle★=★=★ Successfully Repaired Phones by FULLFLASH
EVA-L19 FRP remove success
EFT Dongle
Connecting Fastboot .......
Connecting Fastboot .......Ok
Model Phone: EVA-L19
SW: :EVA-L19C636B390
Connecting Server .....
Connecting Server .....Ok
Erase Done , The Device Will Reboot And Factory Reset
By EFT Dongle OK
EVA-L19 FRP remove success
EFT Dongle
Connecting Fastboot .......
Connecting Fastboot .......Ok
Model Phone: EVA-L19
SW: :EVA-L19C636B390
Connecting Server .....
Connecting Server .....Ok
Erase Done , The Device Will Reboot And Factory Reset
By EFT Dongle OK
 )
)