- Joined
- Dec 1, 2019
- Messages
- 182
- Reaction score
- 204
- Points
- 201
- Location
- brgy. 2 Salcedo eastern samar
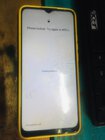
pwer off phone
open mtk client
@ oppo-----a15----factory reset ---start
sundan
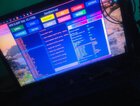
OPERATION: Format Data
1.Turn Off Phone
2.Hold VOL+ And VOL- Then Insert Usb Cable
3.Phone must have battery inside!
Waiting For Device .....
Device -Found
CPU -MT6765(Helio P35/G35)
HW version -0x0
WDT -0x10007000
Uart -0x11002000
Brom payload addr -0x100a00
DA payload addr -0x201000
CQ_DMA addr -0x10212000
Var1: -0x25
Disabling Watchdog.. -OK
HW code -0x766
Target config -0xe5
SBC enabled -True
SLA enabled -False
DAA enabled -True
SWJTAG enabled -True
Root cert required -False
Mem read auth -True
Mem write auth -True
Cmd 0xC8 blocked -True
HW subcode -0x8a00
HW Ver -0xca00
SW Ver -0x0
ME_ID -1B2EFEF3BB4C973060982D49FFF65EC4
Auth Bypass -OK
Device -Found
Device Protected -OK
BROM mode -Connected
Successfully received DA -OK
Sending EMI data -OK
Uploading stage 2 -Done
Successfully stage 2 -OK
EMMC FWVer -0x0
EMMC ID - DX68MB
CID -150100445836384d4209d008e81bb78d
EMMC Boot1 Size - 0x400000
EMMC Boot2 Size - 0x400000
EMMC GP1 Size - 0x0
EMMC GP2 Size - 0x0
EMMC GP3 Size - 0x0
EMMC GP4 Size - 0x0
EMMC RPMB Size -0x400000
EMMC USER Size -0x747c00000
DA-CODE - 0x666D0
DA Extensions successfully -OK
Formating Data - OK
bunot nyo na pad ok na..

pag may frp
emergency call dial *#813#

done done done hit the like thank you pa share narin mga boss